Sunday, March 17, 2019 ~ TECH (global).
~ Web-sourced info, edited by West Shore Voice News
Also see (Links to come): Securing Email on your phone | Securing Text messages on your phone
Most digital tech experts say it’s important that your smartphone be secure, for many reasons. You may keep data on it and if your phone was lost or stolen, this would be lost. Or perhaps your personal information may be hacked from internet pages you have visited or from the smartphone itself. Or perhaps there are people in your sphere who might borrow your phone to look at photos, but end up seeing more.
Don’t ride your phone bareback. Saddle up! Here are some tips to help keep your device as secure as possible.
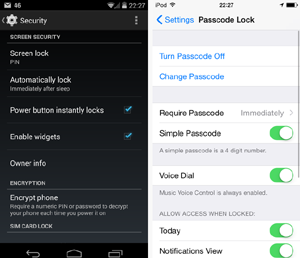
 1. Use a screen lock
1. Use a screen lock
Many new phones offer a “pattern lock” – a personalized shape or pattern that is drawn on the screen to grant access. However, ensure that the screen is cleaned regularly. If your phone is stolen or lost any finger traces can sometimes be seen and accessed on the screen.
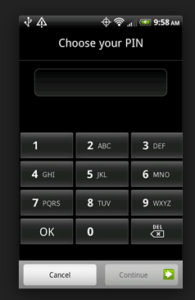
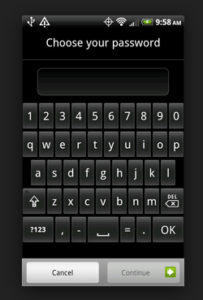
Using a PIN code is easy to set up. On each use of your phone, the extra few seconds of inconvenience for typing in a passcode is probably going to be worth it at some point. Create a password that is difficult to crack but memorable for you.
Remote tracking can be used, if you lose your phone. On Android it is called ‘Find my Device’ and on Apple iPhone it is called ‘Find my iPhone’. From there, your phone can remotely disabled as required.
2. Use a SIM card lock
A screen lock is helpful but won’t stop someone removing the SIM card from your phone and using it on another phone. To prevent this from happening, set up a SIM card lock in the form of a PIN number that will need to be entered when a phone is turned on in order to connect to a network.
 3. Protect sensitive data
3. Protect sensitive data
PIN entry and password locks are helpful, but a smartphone is a computer with easily removable storage. A smartphone can be plugged into a computer or its microSD card can be removed.
It’s important to protect sensitive data that has been saved to internal storage of your phone. Software is available that can encrypt files or folders so that a code must be entered before a file can be viewed or copied. This type of software is free to download and use for automated protection. One example is AutoKrypt but there are others.
To back up your phone data: for iPhone do a backup onto iCloud. Or store data on Dropbox or OneDrive.
4. Wireless protection
Any device that’s can send data across the airwaves comes with a natural concern for security.
Always switch off your wireless connection (e.g. use airplane mode) when it’s not in use. It ensures that people can’t connect to a device without your knowledge. Check your phone’s network security settings; it might be configured to automatically connect to a network when in range without you knowing.
Ensure that your home accessed wireless router is protected by a pass code. If using mobile wireless or a hotspot, be careful of malicious connections that looks very much like a legitimate hotspot from a large company.
5. Protect bluetooth use
Bluetooth isn’t generally seen as a risk as it has a relative shot range (10 metres approx). However, hackers can remotely access a phone if they are in range.
Ensure that bluetooth is turned off when not in use. Set the bluetooth configuration to ‘non discoverable’, so that people searching for nearby devices can’t see yours.
Any unknown requests that pop up through a bluetooth connection, such as an offer to ‘pair with a device’ should be ignored or declined. A hacker in range could make use of your device through bluetooth if it is not secured.
 6. Application download security
6. Application download security
The increase in malware relating to smartphones has increased the need to be cautious when downloading applications. Pay attention to the requirements that any software requires when you install. It can be very easy not to read anything in an effort to get the app up and running, but be careful of any demands to access various features of your phone, particularly if the app isn’t well known.
7. Internet browsing
When accessing a web browser on your smartphone, it can be easy to accept messages that pop up. Agreeing to save user details and passwords might make it easy to remember for later, but unfortunately others can do the same if they gain access to your phone. Also, places you browse through your phone can ‘remember’ your phone and access pathway, as a way to maintain connection or get back into your phone later.
If any security warning pops up when looking at a website, take note of it and leave the website if needed. Also, ensure any banking or shopping sites where you put in secure information have a padlock in the address bar to ensure that the site is encrypted.
 Make sure you always look at the URL and make sure the ‘http’ has an ‘s’ at the end. This ensures that the URL you are about to click on is secure. Check for any spelling mistakes in the URL, so you don’t end up connecting with an unintended site.
Make sure you always look at the URL and make sure the ‘http’ has an ‘s’ at the end. This ensures that the URL you are about to click on is secure. Check for any spelling mistakes in the URL, so you don’t end up connecting with an unintended site.
Also, using URL shorteners (such as bit.ly…) might be handy for sending a long link to someone, but could expose you to privacy invasions and malware attacks.
8. Turn off geotagging
Many smartphone social networking apps automatically upload photos to the Internet. The problem with this is that many phones embed location tags, also called “geotags,” right into the photo files themselves.

Anyone with the right software can look at your Facebook or Flickr pictures and find out where you have been and where you are right at that very moment.
The geotagging feature can be turned off on most phones which gives you privacy and ensures that you can’t be found by someone you might not wish to be found by.
To assure locational privacy when taking photos, don’t use a smartphone. Carry a regular camera for that purpose.
9. Install antivirus
The capabilities of smartphones are approaching those of a PC, but most people have no form of protection, although they can face similar threats.
Spam containing malware attachments or links to attack sites or infected apps that exploit weaknesses in the operating system are all starting to appear.
Many antivirus companies now offer free versions of their commercial mobile products and also protection for multiple PCs and a phone, for a yearly subscription.
Fake antivirus software (designed to infect your device or make you think it’s protected when it’s not), has also now made its way to smartphones. Make careful software choices.
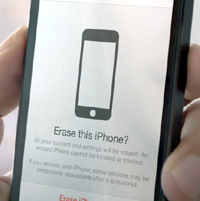 10. Remote wipe
10. Remote wipe
If your phone is lost or stolen, you may want to protect your data by wiping data quickly and remotely.
Many operating systems have a range of third-party, dedicated remote wipe applications to choose from. These tend to be subscription services.
Alternatively, there are other features offered by antivirus packages. Free versions, like AVG’s Mobilation Free, offer local wipe facilities. However, it’s not always clear if remote wipe is included or just a local wipe facility, so check with the software vendor before purchasing.